Over the past few years, the practice of phishing, the attempts by Internet attackers to illegally obtain sensitive information, has dramatically increased.
According to fresh information from Osterman Research, since mid-2014 phishing has been the number one vector for infiltrating a network with malware. So what can you do to prepare your employees against phishing scams? Because all you need is a single employee to click on that link or download that attachment.

To understand what protections you can put into place, it is important to understand the stages of delivering a phish. There are four major stages to a phishing campaign as shown below.

The first stage is generating a list of email addresses that the criminal is going to phish. Some may believe that it is a quantity of quality addresses, others will play the odds. While there are many different ways to generate lists, I want to focus on a category of hacking tools called harvesters. Email harvesters are programs in which one will enter a domain name and the program will scour the internet looking for email addresses and then compile a list. These tools will even provide a list of employees found on LinkedIn where the “quality criminals” will get to know their future victims more intimately and customize the phishing campaigns to them. This is commonly called spear-phishing.
Now that the email list has been generated, the criminals need to decide how they are going to send the phishing email. They have to decide if they want to spoof an email address or purchase a valid domain name. Email spoofing is the forgery of an email header so that the message appears to have originated from someone or somewhere other than the actual source. These can be some of the most difficult to identify with the human eye because the “from” address can look EXACTLY like the one being spoofed.
Once the emails have been sent and delivered to the potential victims, the criminal waits to see how effective they are in convincing someone to click the link, download the attachment, or send the requested information to carry out their final objective.
So what can you do to protect your employees from falling prey?
First, it is important to understand that security should be applied in layers. There is no “silver bullet” or single solution to immunize yourself. Below is a figure showing the opportunities to protect yourself from the stages of a phish.
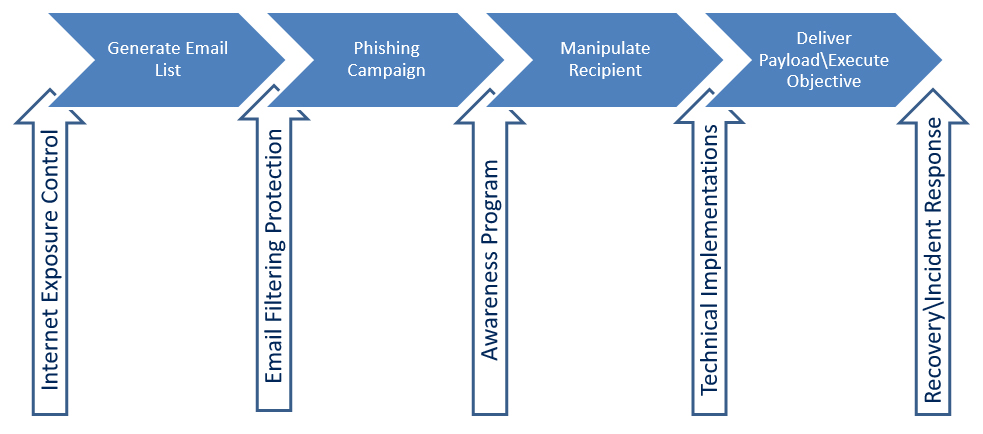
Controlling the proliferation of your organization’s email addresses across the Internet is necessary and very under-discussed. Go to just about any law firm’s or accountant firm’s website and you are almost guaranteed to see everyone’s biography including his or her email addresses. Could you make it any simpler? I will concede that there is a “not-so-good” reason that it has to be there. But here are ways that you can still have your email addresses out there with some degree of protection:
- Create an alias! – An alias is an alternative email address that can only be used for inbound delivery to a real email address. Most organizations are using <first initial><last name>@<domain> these days. Create an alias for <first initial><middle initial><last name>@<domain>. Then have your employees’ set up a mail rule that any emails sent to the alias email address go to a different folder than the inbox. Finally, educate your employees that any emails that are delivered to that custom folder should be treated with extra scrutiny because they are available to the public.
- Use an image! – Since email addresses are text in nature, most websites have them displayed as text on the website. This is done using html most of the time. This is what the email harvesters count on. They know an email address uses the syntax <user>@<domain>. Often email harvesters will search the website code looking for text in the format <user>@<domain> where the <domain> equals what was entered by the criminal. By using an image, the text cannot be extracted easily.
- Use JavaScript! – Okay, this one is technical. However, if you tell your website developer to make sure all email addresses are displayed using JavaScript instead of html, mission accomplished. The reason for this recommendation is because JavaScript does not use the same syntax as <user>@<domain> behind the scenes to have it displayed as such to the web visitor.
- Go For ASCII! – ASCII codes are translated by browsers into the readable character form for visitors. However, they will reduce the chances of a spam bot or harvester picking up the address.
- Use Contact Forms! – Secure email forms are the best and most professional way to protect email addresses while soliciting information. You can even implement a further barrier of a CAPTCHA to prevent auto-populating bots from attacking the system.
- Create Policies! – Granted you don’t always have control of how the website is developed. But what if an employee’s work was published or recognized by a newspaper or magazine? This is why you need to have an alias address or a general mailbox like contact@domain. Create a policy on which email addresses are allowed to be used on the public Internet.
Okay, your Internet exposure is under control; however, a business that you email frequently was hacked and the criminals compiled your email list through that channel.
What can you do to prevent the phishing campaign from being delivered?
Many email providers offer email filtering with their email package. This basic filtering, however, is not sufficient for sophisticated phishing attempts. For less than a dollar per month per email address you can implement a filtering system that not only filters inbound emails but also outbound. Perhaps you do not think about filtering outbound emails, but imagine the potential liability if one of your emails was hacked and used to send malware to your customers, clients, vendors, or other companies. You can look into services such as EveryCloud, MailRoute, or Barracuda.
These are some of the reasons why it is important to consider security in terms of layers. What everyone has learned in recent years is despite all of the sophisticated technical measures we can implement, there always seems to be a way around it. That is what social engineering is based on. Sometimes the easiest way to figure out a password is to ask for it! Implementing a security awareness program has become one of the most important things you can do, regardless of size or industry.
Security Awareness Programs have evolved over time. Until recently, most training has been done without continual monitoring of one’s Internet vigilance and savvy. Effective training these days includes components that are embedded into employee’s daily activities. Take, for instance, a simulated phishing email. If an employee clicks on the link or opens the attachment, it will take them to a remedial training page on why they should not have responded to the attachment. The system will also report to management which employees fell victim to the phishing. When employees know their company sends simulated emails sporadically, they tend to think twice for fear of being reported. In addition, it serves as a continual reminder to be careful. For a demo, please contact us.
How to apply technical implementations.
Somehow, the criminal managed to generate an email list of your organization, bypassed your email filters, and tricked your well-trained employees. Depending on the final objective, you may still have one more layer of defense: technical implementations. This is where I am usually greeted with a blank stare. For that reason, I will briefly touch on a few more high level protections.
- Firewall protections – Firewalls provide many different mechanisms to help protect your network. Technologies such as sandboxing, GeoIP blocking, network-perimeter antivirus, network intrusion prevention, and access control lists are just a few.
- Prevent executables from running in temporary directories. This can prevent the execution of malicious code when opening an email attachment or going to a malicious website.
- Renaming the default name of vulnerable services such as Volume Shadow Copies will neutralize malware that exploits services by name.
- Implementing role-based permissions will contain the damage any single employee causes to the scope of information to which they have access.
- Creating honeypot shared folders diverts malware to spend time on useless data and increases the time one has to react before useful data is affected.
I hope that you heed these warnings and implement some of the suggestions I’ve outlined. If all has failed and a compromise is success, having an incident response plan will help your company know what to do next. Most organizations only consider the industry they operate in and the regulations that apply to that industry (i.e. HIPAA, SOX, GLBA, PCI). However, there are often state laws that are industry independent and apply to all. Know all your legal requirements in a breach and have a pre-established relationship with a security firm that can respond quickly and identify exactly what was compromised. It could mean the difference between closing the doors or staying in business!
For more information, please contact us.
