You work for a small to mid-sized business and outsource the support of your IT systems to a vendor. How do you gauge if your vendor is doing the job you pay them to do? How do you know they are implementing proper security measures? Let us face it, these questions become secondary or tertiary to questions like…..”Are my computer systems working properly?” or “What do I need to do, for what client today?”
The problem that I see many businesses face, is the overwhelming needs to worry about in a day. Cyber security is not an immediate requirement, protects against something that may or may not happen, and does not help a company generate business. Most companies by now have realized that the “I’m not a target because….” attitude is not realistic in practice. If you still think this way then please, call me and let us discuss that.
If you are still with me, it is probably because you can relate to the things that I have said thus far. Now, let me explain what you can do that will give you an 80% solution for 20% effort. Many trend research papers have concluded that the majority of compromises these days start with two common modus operandi or “m.o.” for short. As depicted in the figure below, the initial engagement starts with a malicious email or website. From there a victim is found leading to a compromised computer that then allows the perpetrator to carry out their final objective, which can be any number of things.
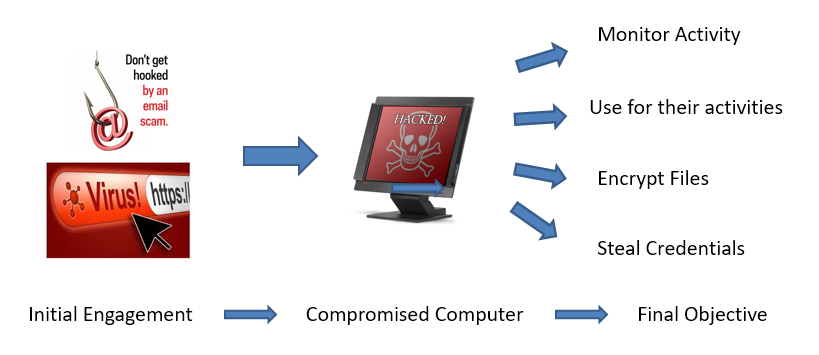
Let us focus on the malicious emails and websites. What is the first thing that must happen to allow a perpetrator to start a phishing campaign? They have to have your email addresses right? If you are interested in seeing how perpetrators generate their email list and what you can do to protect yourself come to one of our upcoming seminars.
After an email list has been generated, what is the next step in a phishing campaign? The perpetrator needs to create a phishing email and have it delivered to the email addresses and wait for their next victim. So what can you do to protect against this step? How about implementing an email filtering system that will not only filter malicious emails but also all of that spam you receive on a daily basis. Who said security can’t help productivity? Imagine the time savings when you no longer have spam or unwanted emails being delivered to your inbox. A word of warning, email filters are not created equally and some are more effective than others. Interested in knowing what to look for in an email filter? Come to one of our upcoming seminars.
Can you guess what the final step of the initial engagement is? It must happen before the computer can be compromised. The victim must fall for the email by clicking a link, downloading an attachment, or responded with the requested information. The defense against this phase is a multi-pronged approach. It first starts with training the employee to identify malicious emails, but let’s say they are still tricked. They are some technical steps that can be implemented to minimize the chances that the malware can execute successfully. If you are interested in knowing more about security awareness programs or these technical steps come to one of our upcoming seminars.
Now that we have talked about malicious emails, what about malicious websites? This as well is a multi-pronged approach as well. It does start with training the employee but also has a technical component. Features such as Geo-IP blocking, Gateway Antivirus, Content Filtering Systems, Intrusion Prevention Systems can sound highly technical and seem to go against the “20% effort” referenced at the beginning. The truth is that it’s not. Vendors have implemented these filters into their firewalls and for the most part can be self-managed. If you are interested in learning more about what these features are come to one of our upcoming seminars.
Hopefully I’ve provided you with insight into the steps of falling victim to cyber criminals and teased you enough to motivate you to come to one of our seminars. I can tell you one thing we excel at…..is visual demonstrations on what cyber criminals do. This helps make “cybersecurity” something that is more tangible increasing your level of understanding and motivate you to take appropriate measures to make sure that you continue to do what you do best.
